ret2libc without ASLR
:material-circle-edit-outline: 约 271 个字 :material-clock-time-two-outline: 预计阅读时间 1 分钟
Stack Canary
Attack
网页服务器一般会 fork 一个子进程来处理请求,子进程的 canary 与父进程一致(因为子进程的栈是直接拷贝父进程的),且模式为 fork-and-accept,故可以不断猜 canary,如果错了子进程会 crush,父进程会断开链接,以此判断,进行 Brute-force Attacks。
Protect
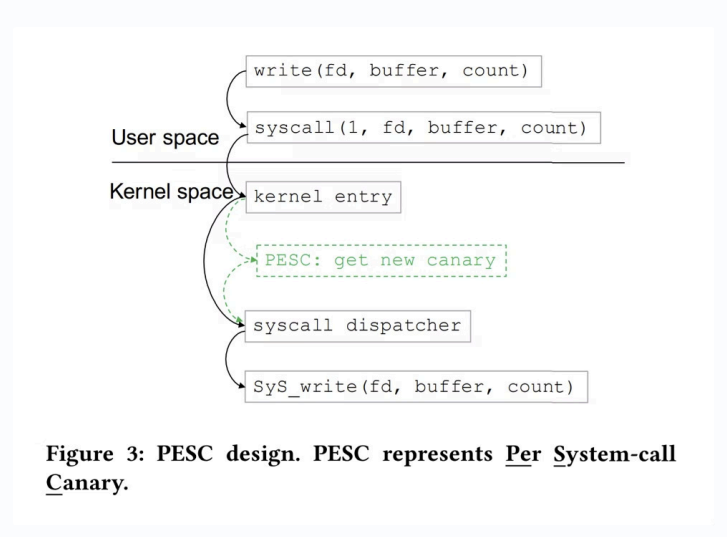
- 子进程更新 canary
- 分内核栈与用户栈
- PESC: A Per System-Call Stack Canary Design for Linux Kernel
Code Reuse Attacks
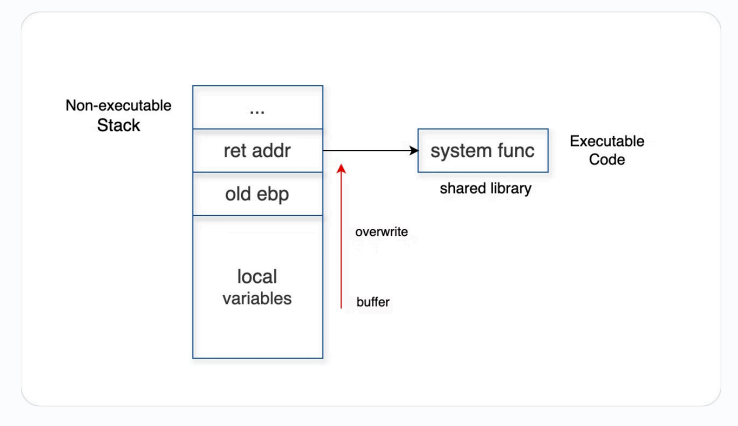
DEP 可以阻止栈上的 shellcode 被执行,我们需要新的方法绕过 DEP
Idea: reuse code in the program (and libraries), No need to inject code
Return-to-libc: replace the return address with the address of a dangerous library function
The attacker constructs suitable parameters on stack above return address
How to Attack
Step I: Find the Address of the System Function

Step II: Find the String “/bin/sh”
Option 1: we can use system environment variables
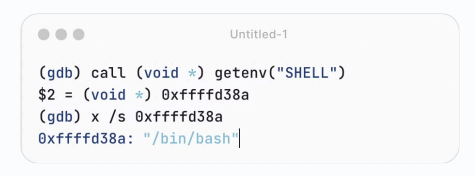
Not stable: the location of this string could change,环境变量每次在进程中位置不固定
Option 2: user–defined environment variables
In fact, libc has this string in its code section
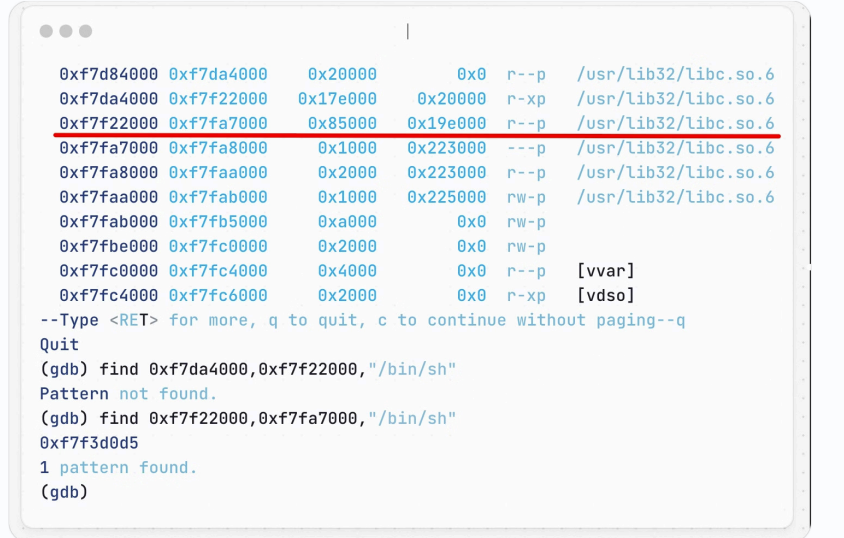
Step III: Invoke system()
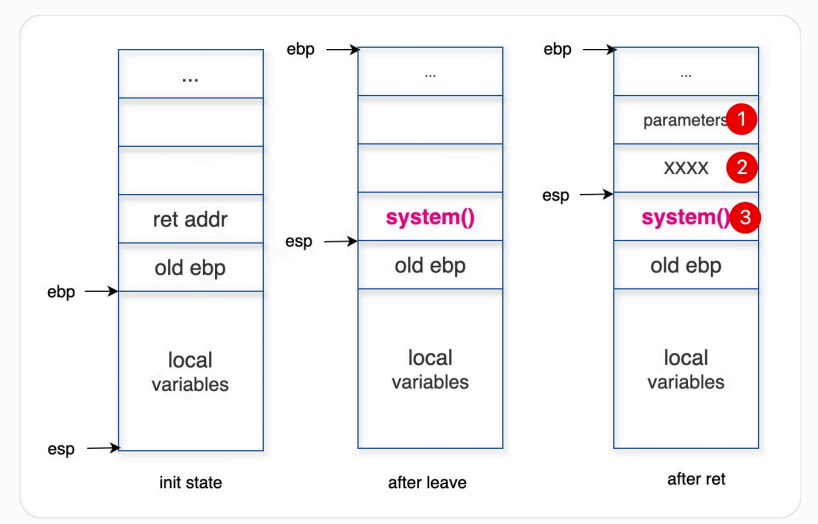
We need to make the stack like this when entering system function()