ret2libc with ASLR
:material-circle-edit-outline: 约 309 个字 :material-clock-time-two-outline: 预计阅读时间 1 分钟
02_ret2libc_with_aslr_32 (gamma.app)
ASLR Makes the Attack Harder, the base address of libc has been changed
→ the address of the system function will be changed
每一次进程调用基地址都会变
How to Get the Base Address of libc
系统三讲过了。。。麻
We can abuse the data in the PLT to leak the library function
- Think about the process to invoke the *printf* function in libc
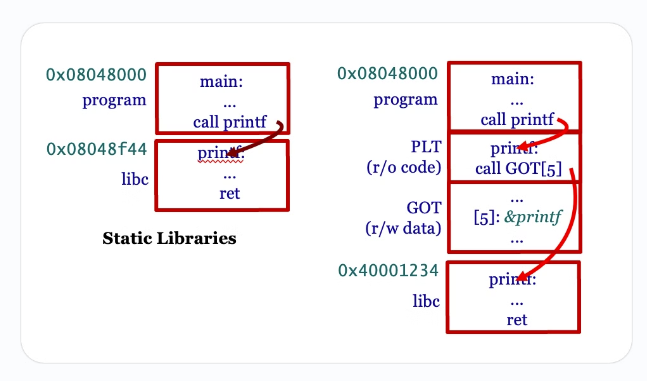
GOT and PLT
???
- Global Offset Table (GOT)
- 这是一个数据区域(data),储存所依赖的外部函数的地址
- To be an indirection table and accessed when PIC calls functions and operates on data variables.
- The values in GOT (Global Offset Table) will be evaluated at runtime by the linker
- Procedure Linkage Table (PLT)
- 每一个外部依赖函数都会在里面,调用外部函数时实际上是调用 PLT,PLT 从 GOT 取出对应函数的地址并跳转
- supporting dynamic linking, adds a level of indirection for function calls analogous to that provided by the GOT for data
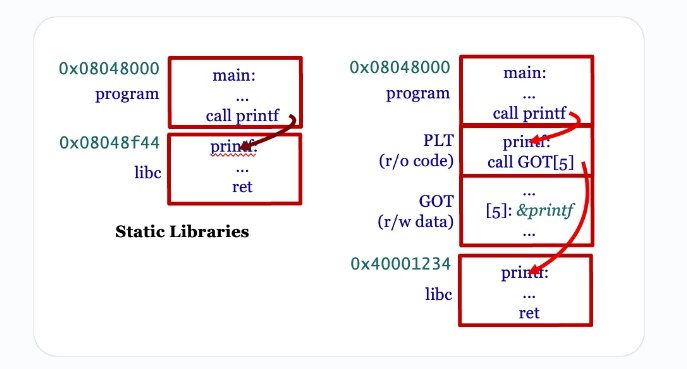
PLT 地址是固定的,我们可以控制 PLT 的 retaddr
we can execute puts(GOT(puts)) → we will output the content stored in the GOT entry, which is the real address of the puts function in libc!

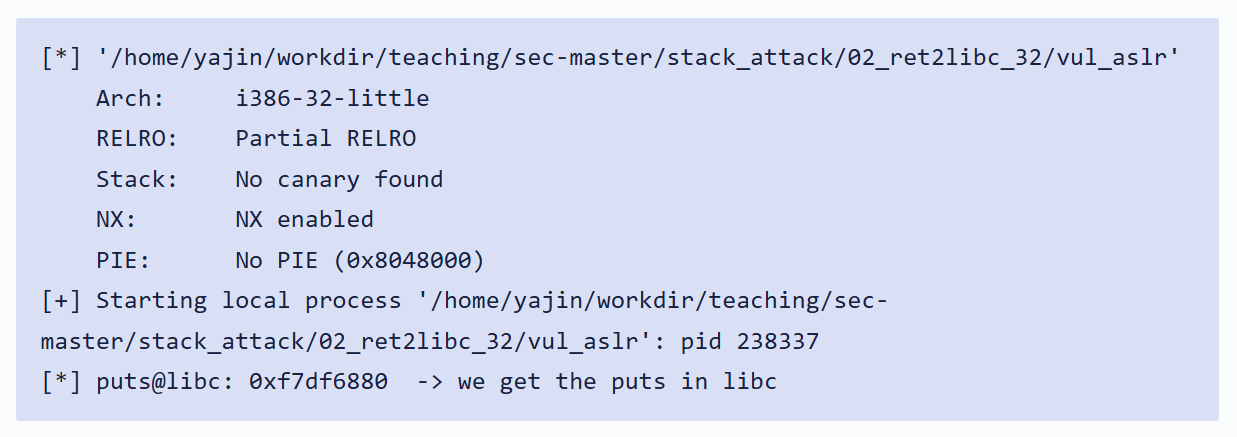
这个地址由于ASLR,每次运行都会变化,所以我们在获取了地址之后应该立即进行下一步操作
Chain Together
????
So far, we can get the base address of libc and other critical functions, including system()
